24. April 2025
A New Chapter in Kubernetes Security
On the 24th of March 2025, the Kubernetes and broader cloud-native community was alerted about a critical set of remote code execution (RCE) vulnerabilities in the widely used Ingress-NGINX controller. Collectively referred to as IngressNightmare, these CVEs revealed the potential for attackers to expose sensitive data, disrupt internal services, and compromise entire Kubernetes clusters in worst-case scenarios.
As part of our ongoing commitment to data protection and infrastructure security, brighter AI initiated an immediate and comprehensive investigation into our exposure. This blog outlines the nature of the vulnerabilities, how we assessed our infrastructure, and the steps we’re taking to protect our systems and customers.
Understanding IngressNightmare: What’s at Stake
Ingress-NGINX acts as the gateway for HTTP/HTTPS traffic, for our scenario, into Kubernetes clusters. The vulnerabilities disclosed include a mix of annotation misuse, webhook misconfiguration, and privilege escalation vectors:
- CVE-2025-1097, CVE-2025-1098, CVE-2025-24514: These vulnerabilities allow attackers to manipulate ingress annotations to alter routing logic or execute arbitrary code (CVSS 8.8).
- CVE-2025-24513: Improper input validation could be combined with other issues to escalate access to privileged Kubernetes resources (CVSS 4.8).
- CVE-2025-1974: The most severe vulnerability. It is enabling unauthenticated attackers with access to the pod network to run arbitrary code, potentially exposing cluster-wide secrets (CVSS 9.8).
Security Community Insights
According to the detector of the vulnerabilities Wiz Research, these vulnerabilities can be exploited through crafted Ingress resources that appear legitimate to the Ingress-NGINX controller. This makes detection difficult, as the configurations use syntactically valid patterns that may evade traditional scanning tools.
The official Kubernetes CVE advisories confirm the severity, especially in environments where the admission webhook of Ingress-NGINX and permissive annotations are present. They emphasize that the complexity of these vulnerabilities requires immediate action by either disabling the Ingress-NGINX Admission Webhook or updating to the new patch release.
How brighter AI embodies Privacy by Design
We conducted a full assessment across both brighter Redact Cloud SaaS and on-premise deployments. Our findings confirm that our security posture minimized a potential external vulnerability as much as possible, thanks to the following ‘Privacy by Design’ principles:
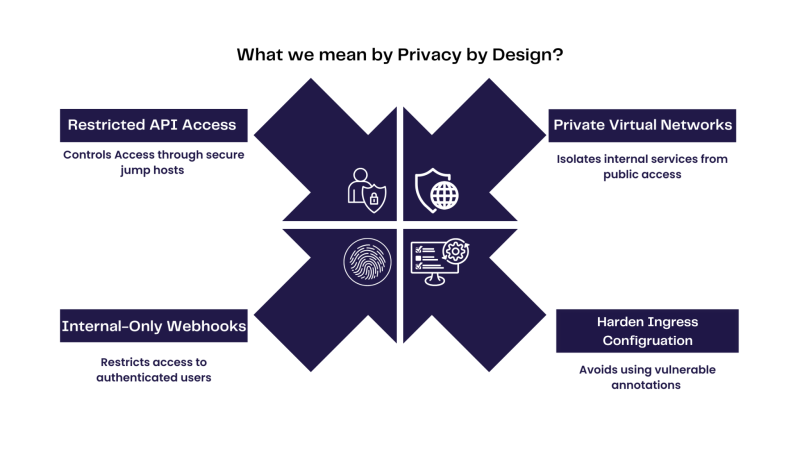
- Private Virtual Networks: All internal services are isolated from the public internet, limiting external access by design.
- Hardened Ingress Configurations: Our ingress rules do not utilize the vulnerable annotations (e.g., auth-url, auth-tls-match, mirror-target, mirror-host).
- Internal-Only Webhooks: The admission webhook of Ingress-NGINX is never exposed externally. It is accessible only by authenticated and authorized services and users operating within our RBAC-secured clusters.
- Restricted API Access: Kubernetes API access is tightly controlled. In our Azure deployment, for example, access is only permitted through a secure jump host within a dedicated private network.
Example: api.brighter.ai (Azure Cloud)
As already introduced, due to our architecture, access control, and configuration, our cloud services do not present any open attack vectors tied to these CVEs. Further, we have investigated our Ingress-NGINX controller logs for potential exploits.
Our Response Plan: Mitigation & Resilience
While our external exposure was highly likely non-existent, we have taken a comprehensive and proactive approach to remediation:
Deployment Updates
Our cloud-managed services exposed via api.brighter.ai have been updated to Ingress-NGINX v1.12.1. Customers using on-prem or private cloud solutions have been contacted individually to schedule coordinated maintenance windows.
Compatibility & Rollback Strategy
We recognize that regulated environments require stability. Therefore, we:
- Perform rollout testing in mirrored staging environments.
- Maintain version-controlled configuration backups.
- Provide rollback support and changelogs to all enterprise clients.
Customer Outreach
We have initiated direct communication with enterprise customers and are prioritizing outreach to sectors with heightened risk profiles.
Continuous Monitoring
We are actively scanning ingress traffic and usage patterns for signs of abuse.
Learn More
- Wiz Research: IngressNightmare Technical Analysis
- Kubernetes Blog: CVE-2025-1974 Advisory
- GitHub Security Advisories (GHSA)
Contact Us
IngressNightmare is a reminder of how fast vulnerabilities can surface and why ‘Privacy by Design’ is essential and no longer optional. At brighter AI, we are continuously monitoring and improving our security posture.
Are you an existing customer and still have doubts about being affected? Then, please reach out to our support at any time: [email protected]
For everyone who is looking to anonymize sensitive visual data for data privacy compliance, please reach out to our sales team at [email protected]. We will help you select and tailor the right anonymization architecture for your specific needs, ensuring you protect sensitive information without compromising on performance.
Stay compliant,
The brighter AI Team




